On Windows, when you try to open or run an exe, msi, bat, cmd (and other file types) executable file from a local drive or network share, you may receive a warning “ Open File - Security Warning”(Open file - Security Warning). To continue the execution of the program, the user must manually confirm the launch of such a file by pressing the button “ Run” (Run). This Windows security warning usually appears when you run an application installation file or executable file downloaded from the Internet that is located on a shared network folder on the server.
This Windows setting is designed to protect your computer from running potentially dangerous executable files that you have downloaded from the Internet or other untrusted sources and are trying to run. This feature when launching files is present in both Windows 7 and Windows 10.
In some cases, when the launch / installation of such software is carried out in the background through scheduler scripts, group policies, SCCM tasks, etc. this can cause problems because the warning window is not displayed in the user's session. Accordingly, installation or launch of such an application from a script becomes impossible.
Recall what the warning window looks like. For example, when opening a file from a network directory, the Windows Security Warning window looks like this:
Unable to verify publisher. Are you sure you want to run this file?
Open File - Security Warning
The Publisher could not be verified. Are you sure you want to run this software?
When running a file downloaded from the Internet from a local drive (or a network directory mounted via net use), the warning text is slightly different:
Open File - Security Warning
Do you want to run this file?
Open File - Security Warning
Run this file?
Files from the Internet can be useful, but this type of file can damage your computer. Only run programs from a trusted publisher.

Let's try to figure it out how to remove security warning when running executable or installation files in Windows 7 and Windows 10 (the instruction is also suitable for all other Microsoft operating systems, starting with Windows XP).
Important. Disabling this window with a Windows security warning is not recommended in most cases, as it reduces the level of computer protection and increases the risk of user infection of the system.
We offer several options to disable the security warning window. Choose the appropriate method depending on the required solution (in some cases, the proposed solutions have to be combined).
Disable the warning window when launching a file downloaded from the Internet
Executable files downloaded from the Internet are automatically marked as potentially dangerous (downloaded from an unsafe source). This functionality is implemented through alternative NTFS file streams. To simplify, we will assume that this is a special file label that is automatically assigned to a file downloaded from the network (). To remove this label, you need to unlock this application. For this:

Save the change by clicking the Ok button. Once the file has been unlocked, it will run without a warning window (NTFS tag will be removed).
Trick. To prevent the label from being automatically assigned to files that you download from the Internet through a browser, you can save the downloaded files to a disk formatted in the FAT32 or . On these file systems, NTFS alternate streams do not work.
The label of the alternative NTFS stream Zone.Identifier can be reset using the following two commands (a new file will be created):
move oldName.exe > newName
type newName > oldName.exe
Or utilities
streams.exe
If you want to disable this warning only for files downloaded using a browser, then you can disable saving the Zone.Identifier attribute when downloading files directly in the browser:
For Google Chrome and IE, you need to create such a registry key
“SaveZoneInformation”=dword:00000001
And for Mozilla Firefox on the settings page about:config change browser.download.saveZoneInformation value to false.
Security warning when running applications from a network directory
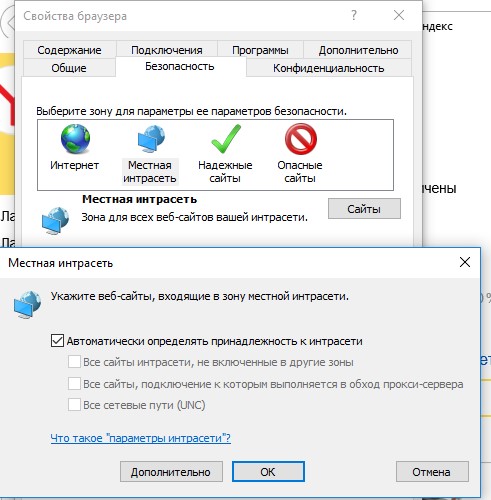
This option typically occurs with corporate users who work on an organization's network. A warning window may appear when starting the program from a shared network directory (network shares) via a UNC path. In this case, the easiest way is to add the name and / or ip address of the server on which the executable file is stored in the Internet Explorer settings to the zone Local intranet. This will indicate that this resource is trusted. For this:
You can add addresses of network directories and servers to the Local Intranet zone using Group Policy (GPO). Open the local (gpedit.msc) or domain (gpmc.msc) policy editor. Go to Compute Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page (Computer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Browser Control Panel -> Security Tab ). Enable policy Site to Zone Assignment List(List of website security zone assignments). In the policy settings, you need to specify a list of trusted servers in the format:
- Server name (as file://server_name, \\server_name, server_name, or IP)
- Zone number (1 - For local intranet)

Save the changes to the policy and update it on the client (gpupdate /focre). The warning when opening executable files from specified network directories should stop appearing.
In addition, the following settings can be enabled in group policies under User Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page (User Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Browser control panel -> Security tab). This is the best option for domain users:
- Intranet Sites: Include all local (intranet) sites not listed in other zones
- Intranet Sites: Include all network paths (UNCs)
- Enable automatic intranet detection
Disabling warning for certain file types via GPO
In some cases, it is advisable to disable the warning for certain types (extensions) of files through group policies. Although, of course, this is not very safe, because. the user can run something malicious without looking.
To do this, in the GPO editor, go to the section user Configuration-> administrative Templates-> Windows Components-> attachment manager(User Configuration -> Administrative Templates -> ComponentsWindows-> Attachment manager).
- Enable policy Do not store information about the zone of origin of attachments(Do not preserve zone information in file attachments). All executable files downloaded from the Internet will run without confirmation on all computers.
- Enable policy Include list for low-risk file types(Inclusion list for low file types), specify in its settings a list of file extensions for which you want to disable the appearance of a window with a Windows security warning, for example: .exe; .vbs; .msi. The system will ignore labels on files with this extension and run them without confirmation.
Note. In this case, these file extensions are added to the LowRiskFileTypes registry value: "LowRiskFileTypes"=".exe;.vbs;.msi;.bat;"

Save the policy and apply it to clients by running gpupdate /force on them.
After that, the warning should stop appearing when opening files with the specified extensions with any information in the Zone.Identifier attribute.
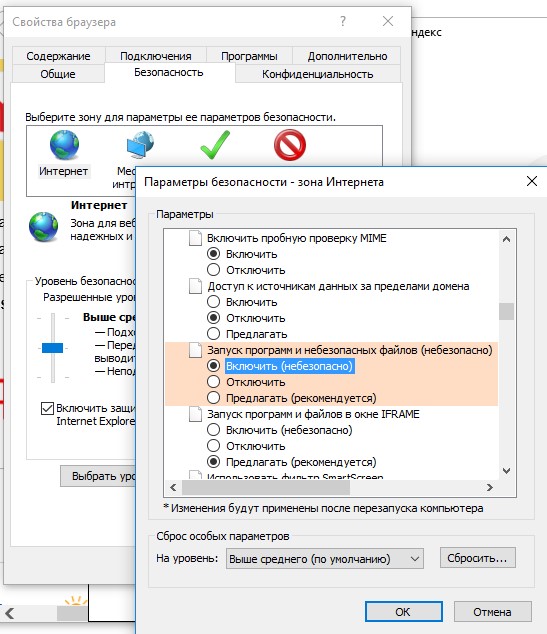
You can also allow the launch of any files from the Internet in the browser settings for the Internet zone (Security - .Internet -> Other -> Miscellaneous -> Starting programs and unsafe files), but this is extremely risky.