Friends, hello. Today's article will be useful primarily for corporate users of Windows-based computers working with standard local accounts. Whereas access to accounts with administrator status can only be performed by authorized persons of the company in the form of employees of the IT section. Although in a certain family microclimate, the problem described below can be encountered using home devices. What kind of problem is this? And this is the inability to access Windows with a notification on the lock screen "The user account has been blocked and cannot be used to log on to the network." What kind of blocking is this, and how to deal with it?
So, we cannot enter Windows, because we see this on the lock screen.
Such blocking is the result of a certain number of unsuccessful authorization attempts in the local account, if the computer administrator has made the appropriate local group policy settings.
Windows account lockout
The computer administrator in local group policies can set a certain number of attempts to log on to user accounts. If this number of attempts is exceeded, the account is blocked from logging in. This is such a protection against guessing passwords. Even if we are not dealing with a situation of trying to guess a password for someone else's account, but simply its true owner inattentively entered characters or did not look at the keyboard layout, it will not be possible to enter the system even if the correct password is entered. You will have to wait for the time set by the administrator until the counter of login attempts is reset. And, of course, until the time of the block itself expires.
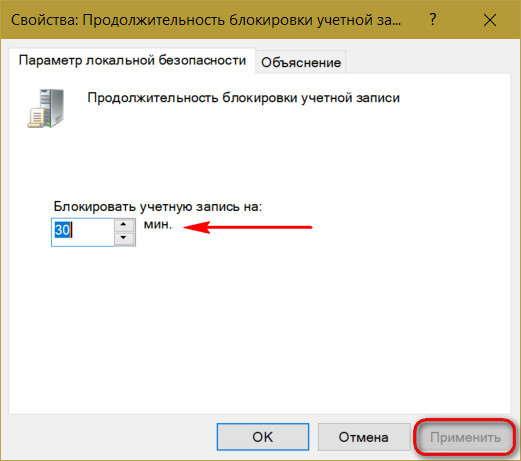
Such protection against password guessing is set in the local group policy editor, in the account lockout policy.
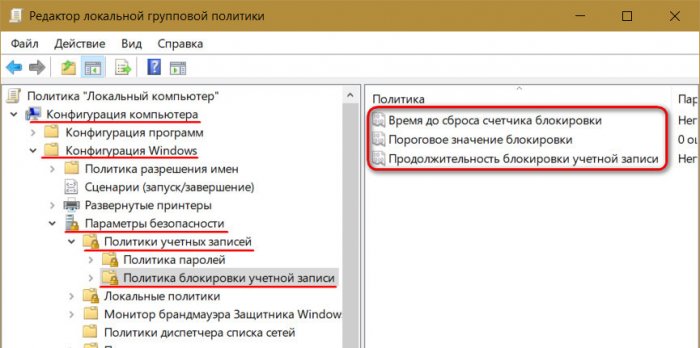
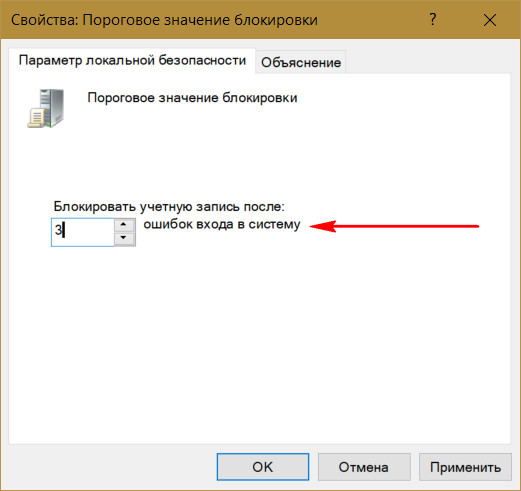
When you set this threshold, other policy settings - the time until the block counter is reset and the duration of the block itself - will automatically be set to 30 minutes.
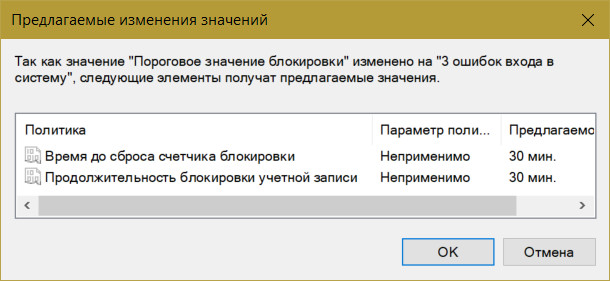
They can be changed if necessary. And, for example, set a shorter time to reset the counter of failed password attempts.
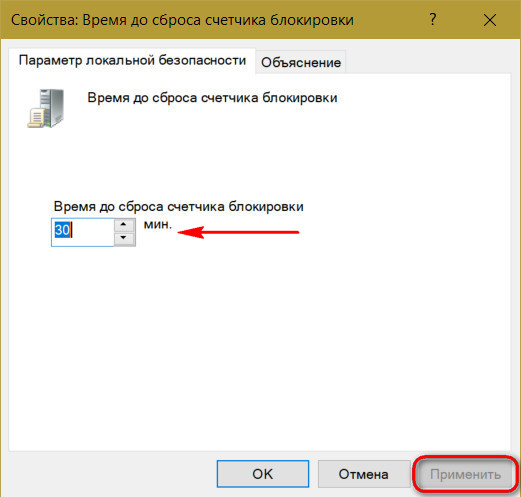
And the time of blocking the account itself, on the contrary, increase.
This protection applies only to local accounts and does not work when trying to guess a password or pin code for connected Microsoft accounts.
You can unblock a blocked account in several ways:
Log in with an administrator account and unlock;
If access to the administrator account is not possible, unlock it by booting from a removable device and tweaking something in the Windows registry.
How to unlock your Windows account if you have administrator access
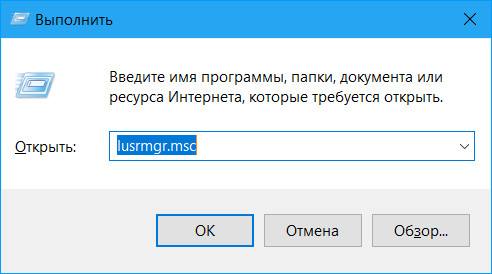
If your account is locked, but you have access to the administrator account, you need to log into the latter and unlock yours in this way. Press the Win + R keys, enter:
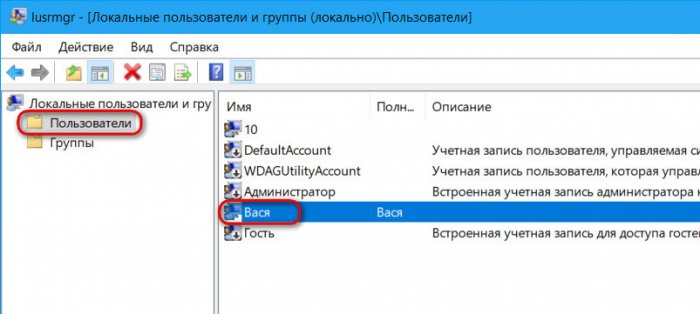
In the window that opens, in the "Users" folder, look for your account and double-click on it.
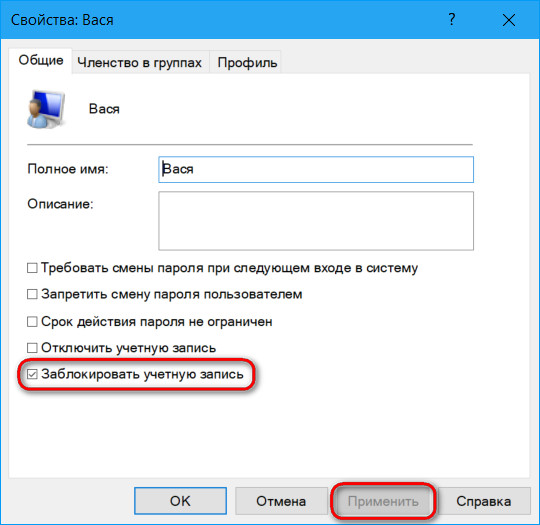
In the properties window that opens, uncheck the "Block account" checkbox. Apply.
We are trying to log into our account.
- Note: if you do not have a password for the administrator account, do not try to enter using the selection. Password protection applies to all local accounts, including the administrator. His account after a certain number of unsuccessful authorization attempts will also be blocked.
How to unlock your Windows account if you don't have administrator access
If there is no access to the administrator account, we get a DVD or flash drive with the installation process of any version of Windows or a Live-disk with the ability to edit the registry of the operating system. We boot the computer from a removable device, in our case it is a Windows 10 installation flash drive. Important: starting from a removable device should be carried out only when Windows 8.1 and 10 systems are rebooted. You cannot use a normal shutdown, because in these versions, due to the accelerated startup function, the system kernel is loaded from a previously saved file on disk. What we need is for the kernel to boot with the modified registry settings.
At the first stage of Windows installation, press Shift + F10. We start the registry with the command line:
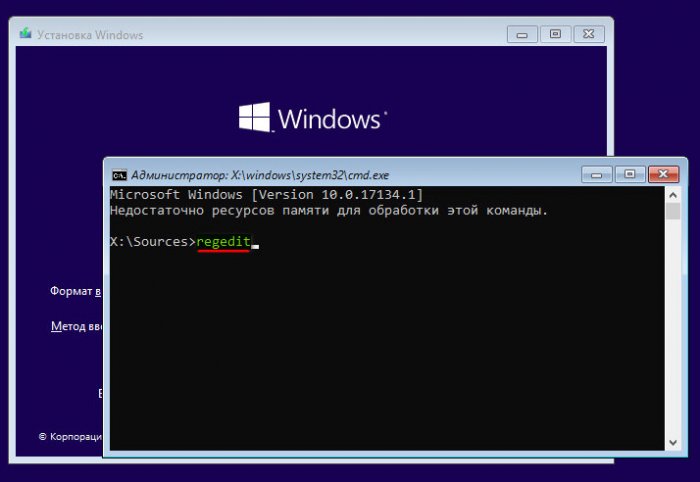
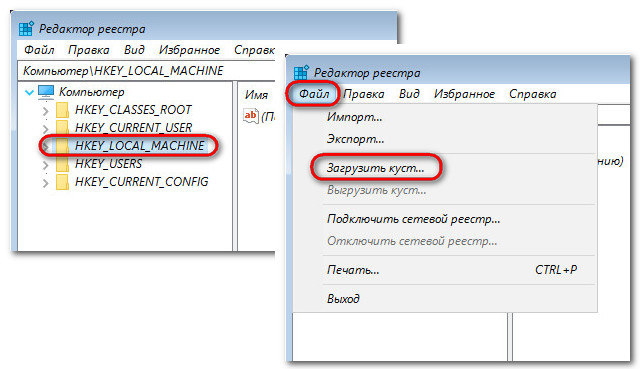
In the overview window, go to the root of the devices "This PC" and go to the Windows section. We have it designated as a drive (C:\), but the system drive can also appear under a different letter. Here you need to navigate by the volume of the section. On the system partition, open the “Windows” folders, then “System32”, then “config”. Inside the latter, we need a SAM file, this is the so-called registry hive, open it.
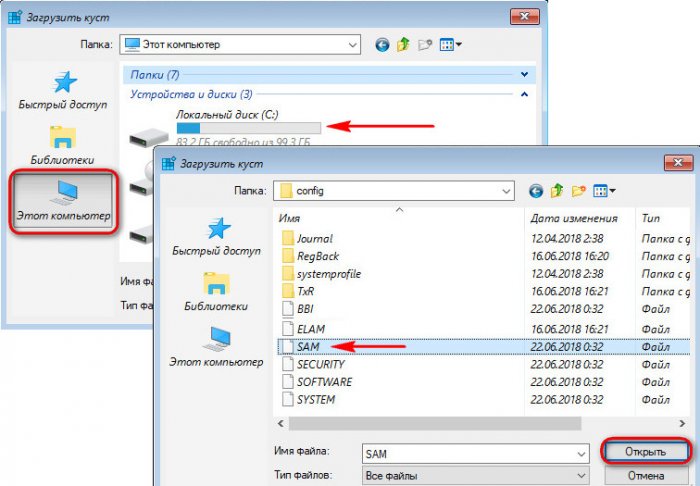
An open bush needs to be named somehow, the name is unprincipled. Let's call it 777.
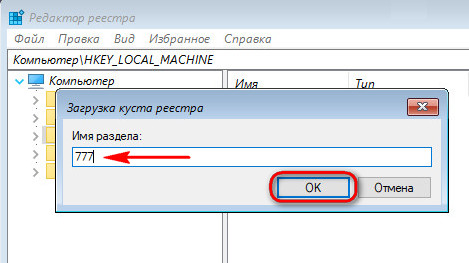
Inside the HKEY_LOCAL_MACHINE registry key, we now observe a new branch 777. We open the path inside it:
777 - SAM - Domains - Account - Users - Names
We find the name of our account in the "Names" folder. For example, we need the user Vasya. We look at what is displayed on the registry panel on the right when Vasya is selected. We have a value of 0x3f8. The same value, but only in a different writing format - with extra zeros in front and caps - we are now looking for higher, inside the "Users" folder.
