Many programs require elevation at startup (the shield icon next to the icon), but in fact, they do not require administrator rights for their normal operation (for example, you manually granted the necessary rights to users on the program directory in ProgramFiles and the registry branches that are used by the program). Accordingly, when you run such a program from under a simple user, if User Account Control is enabled on the computer, a UAC prompt will appear and the user will be required to enter the administrator password. To get around this mechanism, many simply disable UAC or give the user administrative rights on the computer by adding him to the local Administrators group. Naturally, both of these methods are unsafe.
Why would a normal app need admin rights
Administrator rights may be required for the program to modify some files (logs, configurations, etc.) in its own folder in C:\Program Files (x86)\SomeApp). By default, users do not have rights to edit this directory, respectively, for the normal operation of such a program, administrator rights are needed. To solve this problem, under the administrator at the NTFS level, you must manually assign the change / write right for the user (or the Users group) to the folder with the program.
Note. In fact, the practice of storing changing application data in its own directory in C:\Program Files is not correct. It is more correct to store application data in the user profile. But this is a question about the laziness and incompetence of developers.
Running a program that requires administrator rights from a standard user
We have previously described how you can use the RunAsInvoker parameter. However, this method is not flexible enough. You can also use /SAVECRED with saving the admin password (also insecure). Let's consider an easier way to force the launch of any program without administrator rights (and without entering the admin password) with UAC enabled (level 4,3 or 2).
For example, let's take the registry editing utility − regedit.exe(it is located in the C:\windows\system32 directory). When you run regedit.exe, a UAC window appears and if you do not confirm the privilege elevation, the registry editor does not start.

Create a file on the desktop run-as-non-admin.bat with the following text:
cmd /min /C "set __COMPAT_LAYER=RUNASINVOKER && start "" %1"
Now to force the application to run without administrator rights and suppress the UAC prompt, just drag the desired exe file to this bat file on the desktop.

After that, the registry editor should start without a UAC prompt. Opening the process manager, and add a column Elevated(With more high level permissions), you will see that the system has a non-elevated regedit.exe process (running with user rights).

Try editing any setting in the HKLM branch. As you can see, access to edit the registry in this branch is denied (for this user no write permissions to the system registry branches). But you can add and edit keys in the user's own registry branch - HKCU.

Similarly, you can run a specific application through a bat file, just specify the path to the executable file.
run-app-as-non-admin.bat
Set ApplicationPath="C:\Program Files\MyApp\testapp.exe"
cmd /min /C "set __COMPAT_LAYER=RUNASINVOKER && start "" %ApplicationPath%"
You can also add context menu, which adds the ability for all applications to run without elevation. To do this, create the following .reg file and import it into the registry.
Windows Registry Editor Version 5.00
@="cmd /min /C \"set __COMPAT_LAYER=RUNASINVOKER && start \"\" \"%1\"\""
After that, to launch any application without admin rights, just select the "" item in the context menu.
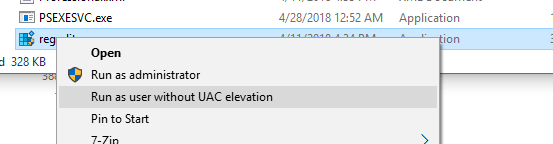
__COMPAT_LAYER environment variable and RunAsInvoker parameter
The __COMPAT_LAYER environment variable allows you to set different compatibility levels for applications (tab Compatibility in properties exe file). With this variable, you can specify the compatibility settings with which you want to run the program. For example, to run an application in Windows 7 compatibility mode at a resolution of 640x480, set:
set __COMPAT_LAYER=Win7RTM 640x480

Of the options of the __COMPAT_LAYER variable that are interesting to us, we select the following parameters:
- RunAsInvoker- launch application with parent process privileges without UAC prompt.
- RunAsHighest- launch the application with the maximum rights available to the user (the UAC prompt appears if the user has administrator rights).
- RunAsAdmin- run the application with administrator rights (the AUC request always appears).
Those. the RunAsInvoker parameter does not grant administrator rights, but only blocks the appearance of the UAC window.
I caught fire with this idea of security and decided to try to do the same for myself.
Since I have Windows 7 Professional, the first idea was to use AppLocker "a, but it quickly became clear that he did not want to work in my edition of Windows, and required Ultimate or Enterprise. Due to the licensing of my Windows and the emptiness of my wallet, the option with AppLocker" om gone.
The next attempt was to set group policies limited use of programs. Since AppLocker is a “pumped” version of this mechanism, it is logical to try policies, especially since they are free for Windows users :)
Let's go to settings:
gpedit.msc -> Computer Configuration -> Windows Settings -> Security Settings -> Software Restriction Policies
If there are no rules, the system will offer to generate automatic rules that allow programs to be launched from Windows folders and Program Files. We also add a deny rule for the path * (any path). As a result, we want to be able to run programs only from protected system folders. And what?
Yes, this is what we will get, but here's just a little bad luck - labels and http links do not work. You can still score on links, but it’s not good to live without labels.
If you allow files to be launched using the *.lnk mask, we will be able to create a shortcut for any executable file, and launch it using the shortcut, even if it is not in system folder. Lousy.
A request to Google leads to such decisions: either allow launching shortcuts from a user folder, or use third-party bars with shortcuts. No other way. Personally, I don't like this option.
As a result, we are faced with the situation that *.lnk is, from the point of view of Windows, not a link to an executable file, but an executable file. It's crazy, but what can you do ... I would like Windows to check not the location of the shortcut, but the location of the file to which it refers.
And then I accidentally came across the settings for the list of extensions that are executable from the point of view of Windows (gpedit.msc -> Computer Configuration -> Windows Configuration -> Security Options -> Assigned File Types). We delete LNK from there and at the same time HTTP and relogin. We get fully working shortcuts and check for the location of the executable file.
There was a doubt whether it would be possible to pass parameters through shortcuts - it is possible, so everything is ok.

As a result, we got the implementation of the idea described in the article "Windows computer without antiviruses" without any inconvenience for the user.
Also, for those who like to shoot themselves in the foot, you can create a folder in Program Files and throw a shortcut for it on the desktop, calling it, for example, “Sandbox”. This will allow you to run programs from there without disabling policies, using protected storage (protection via UAC).
I hope the described method will be useful and new for someone. At least I have never heard of such a thing from anyone and have not seen it anywhere.
Some actions regular programs can be classified Kaspersky Total Security as dangerous. If a Kaspersky Total Security blocking the operation of the program, and you are sure that it is safe, add the program to the list of trusted ones or create an exclusion rule for it.
After adding the program to the list of trusted Kaspersky Total Security stops monitoring the file and network activity of this program, as well as its access to the registry. At the same time, the program executable file continues to be scanned for viruses. If you want to completely exclude an application from scanning, create an exclusion rule for it.
To add an application to the trusted list, do the following:
- In the window Setting go to section Protection and choose Threats and exclusions.
- In the window Threat and exclusion settings click on the link Specify trusted programs.

- In the window Trusted programs click on the button Add.

- Specify the executable file of the trusted application by clicking on the link Review or by selecting a program from the list (displays running in this moment programs).

- In the window Program Exceptions define the parameters for applying the rule by checking the necessary checkboxes:
- Do not check open files- exclude from scanning all files that are opened by a process of a trusted application.
- Do not monitor program activity Activity monitoring any activity (including suspicious) performed by a trusted application.
- Do not inherit the restrictions of the parent process (program) - The program's activity is controlled according to the rules set by the user. If the checkbox is cleared, the program obeys the rules of the program that launched it.
- Do not monitor the activity of child programs- exclude from the check within the framework of the component operation Activity monitoring any activity (including suspicious) performed by child processes of a trusted application.
- Allow interface interactions Kaspersky Total Security.
- Don't scan all traffic- exclude from scanning for viruses and spam network traffic initiated by a trusted application. With the checkbox checked Don't scan all traffic The traffic of the specified application is NOT checked only on viruses and spam. However, this does not affect traffic inspection by the component. Firewall , according to the parameters of which the network activity this program.
- To exclude only encrypted network traffic from scanning, click the link Don't scan all traffic and choose Do not check encrypted traffic, thus only encrypted traffic will be selected (using the protocol SSL/TSL)
- Additionally, you can restrict the exclusion to a specific remote IP address/port:
- To not check a specific IP address, select the checkbox For specified IP addresses only, and then enter the IP address in the field.
- To not check certain ports, select the checkbox For specified ports only Enter ports in the field separated by commas.
- In the window Program Exceptions click on the button Add.

- Close the program windows.
AT Kaspersky Total Security by default to trusted programs with the parameter Do not scan encrypted network traffic added file %SystemRoot%\system32\svchost.exe- system service executable file Microsoft Windows update. The protected traffic of this service is not available for inspection by any antivirus software. If an allow rule is not created for this service, the operation of this service will be terminated with an error.
There are cases when ordinary users need to run certain software or applications that require administrative rights for their normal functionality. At the same time, it is very undesirable to notify the administrative password in such situations and provide an administrative account. But still there is a way out. You can use a very simple, small, and most importantly free utility RunAsTool. This program allows you to grant any level of rights for a specific list of programs.
Let's see how it works.
Immediately after starting the program, you may receive the following message.

This message means that the system does not have a password-protected administrative account. Therefore, if you receive this message, just find the section in the control panel that is responsible for accounts: “User Accounts” and set a password for the administrator account. And also this function can be used directly from the program by clicking on the "Yes" button, which will call the necessary settings window from the system.

After the password is set, you can update the list of Admins by clicking on the arrow button in the program window, or simply restart the utility. In case you have several administrative accounts, then in the drop-down list you can select the one on behalf of which all programs / applications will be launched. Now, in order to configure the utility in edit mode, you will need to enter the password of the selected administrative account.
In the future, these credentials will be used by the utility to run programs as administrator.

In edit mode, it is possible to add programs to the list either using the "File" -> "Add" menu, or simply by dragging the application shortcut to the left window of the utility with the mouse. After that, all the necessary information about the launch of the selected application will appear in the right part of the program window.
The main thing is to make sure that it will run on behalf of the Admin, in case a different setting is set there.

You also need to make sure that this utility is available to run from other non-privileged accounts. But for this purpose, such a setting in the interface as creating a shortcut for the desktop can serve. After choosing this installation, all ordinary users should have a shortcut on their desktops to launch the utility, providing fast access to the list of privileged programs.

When ordinary users will use RunAsTool, they will not see the edit mode. For these users, only a simple window with icons of programs will be available, which they can run with administrative rights. But in the event that it becomes necessary to return to the editing mode and change the list of programs or other settings, then this can easily be done through the menu “File” -> “Enable editing mode”, for which the utility will ask you to re-enter the password.

You can easily verify the performance of this method using the task manager, since it displays information about the user who launched this or that process / application. Where it becomes obvious how applications in one account are launched on behalf of another user.
Sometimes a firewall blocks trusted apps from accessing the internet, but on Windows 10 it's very easy to change the settings to manually allow an app through the firewall. Here's how to do it.
Windows 10 offers a range of security features to help protect your device and data from unauthorized access, malware, and other attacks with a built-in firewall. While the built-in firewall does a good job of controlling which apps and features can communicate over the network, sometimes you may need to allow or deny apps manually.
In this guide, you will learn how to allow or block applications from accessing the network by configuring the firewall in Windows 10.
Allow communication with applications in Windows Defender Firewall.
To enable a trusted app or feature through the built-in firewall in Windows 10, follow these steps:
Step 1: Open " Security Center Windows Defender» .
Step 2: Press "Firewall and Network Security".


Step 4: In the window, press the button "Change settings".

Step 5: In the list, find the app or feature you want to allow through the firewall.
Quick tip: If the application is not listed, click the button "Allow another app" to find the app you want to allow internet access.
Step 6: Choose which type of network the app can access:
- Private: Allows a user to access a network at home or work where users and devices are trusted and known to you.
- Public: Allows the user to access the network in a public place such as a cafe or hotel.
Step 7: Click the button "OK".
After you complete the steps above, the application will now freely access the network.
If you want to block the application through the firewall, you can choose desired application and press the button "Delete" or follow the same instructions, but on step 6 make sure you uncheck the appropriate checkbox for an app or feature if you want to prevent it from accessing the internet.

This guide focuses on setting up Windows firewall 10, but in case you have a different security solution, be sure to check the instructions on the vendor's support site.
